Understanding and Optimizing Sophos XG’s DNAT Rules

by

Etienne Liebetrau
Understanding and Optimizing Sophos XG’s DNAT Rules
Sophos XG makes it easy to expose internal services to the public internet using the Server Access Assistant (DNAT) wizard. However, this does generate a lot of configuration that is not strictly required. By knowing your environment, some basic theory, and what is and is not required, you can configure clean concise DNAT rules.
This article helps you understand the types of NAT available and uses the example of exposing a Plex server on the public internet without the extra DNAT rules that are not needed.
NAT Background
When network traffic moves back and forth between an internal private IP address space (LAN) and a public IP address space (WAN), there needs to be some sort of network address translation (NAT) that occurs.
When configuring any firewall or perimeter device, one of the first steps is to make sure you can connect from your internal network to the internet or WAN for DNS, HTTPS traffic etc. As you don’t want to expose all private IP addresses on the public internet, Source Network Address Translation (SNAT) is required here.
Once internal hosts can access the internet or WAN, the next test is to expose something on the internal network, such as a web server, and make it available from the internet. Since a device on the internet cannot connect directly to a device on someone’s private network, they need to have the traffic forwarded from the perimeter device to the internal device. This process is sometimes called port forwarding or Destination Network Address Translation (DNAT).
Common terminology
SNAT – Source Network Address Translation
The most common form of a SNAT is a masquerade or MASQ rule. It allows for all of the internal addresses to be hidden from the external network. It does this by having a many-to-one relationship of many internal addresses all being translated to the same single external address. All of the source addresses are replaced with the public IP address.
DNAT – Destination Network Address Translation
Typically, DNAT is required when the server is on an internal network and must be accessed through another external IP address on a perimeter device. When traffic is received on the public IP address the destination IP address is replaced by the internal IP address.
PAT – Port Address Translation
Port address translation is not as frequently required. If the internal server is listening on TCP port 32400 and the traffic arrives at the public address on port 32400 then it is just a straightforward 1:1 mapping and no translation is required. PAT can come in handy where you have multiple internal IPs providing a service on a common port number that you need to expose publicly on a single IP address.
Sophos XG Terminology
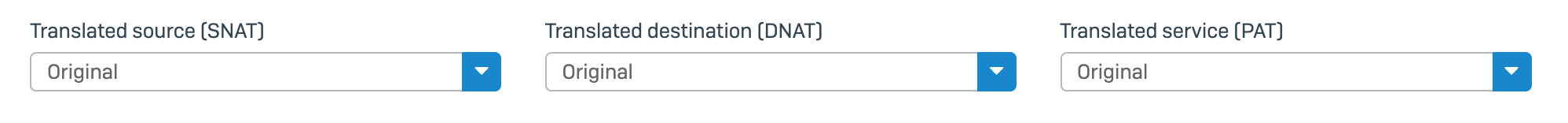
Sometimes, firewalls use different terms in their interface to refer to these industry-standard terms. For example, Sophos XG uses ‘Translated Source’ instead of just calling it SNAT, which would both be more accurate and specific. The terminology is relative to the perimeter device and is determined by the direction of a connection. A connection starting in the LAN requesting a resource on the WAN would have the source as the LAN and the destination as the WAN, and so on.
Configuring DNAT for a Plex media server using Sophos XG
In this article, I’ll take you through configuring DNAT on a Sophos XG firewall for the purpose of exposing an internal Plex media server which may be handy for those using the free Sophos XG Home edition to protect and monitor their home network (Psst: we don’t actively advertise it, but we do offer a home user price for Fastvue Sophos Reporter).Here are the details:
Server’s internal IP address: 192.168.1.151 (Internal name of Minty)
Service: TCP port 32400
The public firewall IP address is 41.193.10.15
The public client IP address 21.45.122.5
For this, to work we need to be able to accept a connection from the internet on TCP 41.193.10.15 on PORT 32400 using TCP protocol and forward it on to the internal server on 192.168.101.99 and then finally for the reply to be able to make its way back to the original public IP address. Fortunately, Sophos XG has an assistant for this.
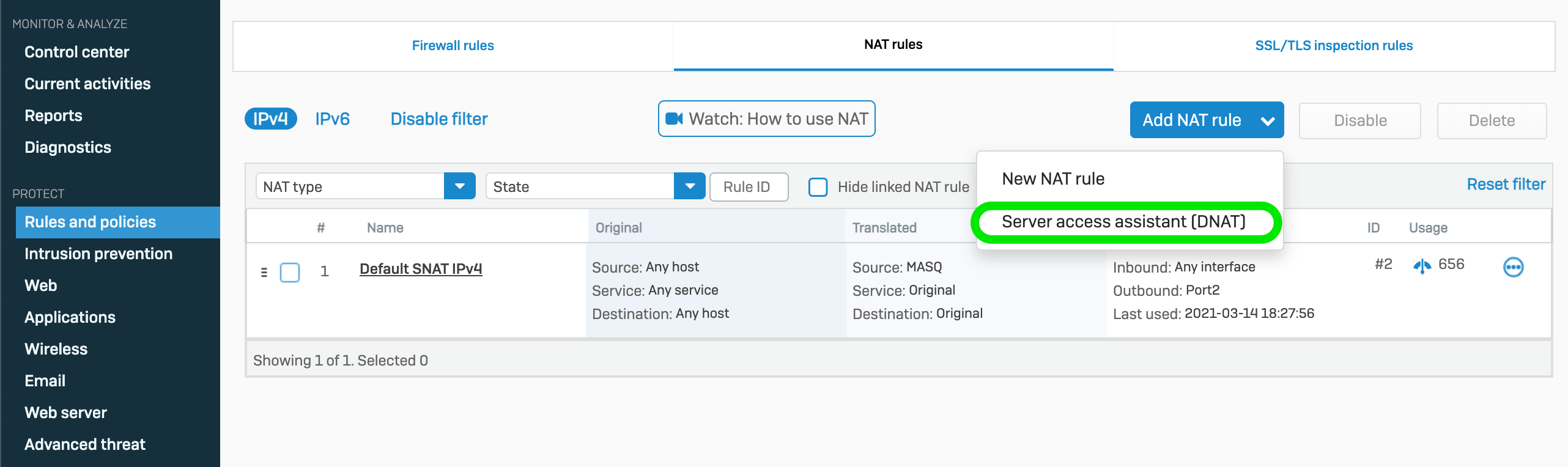
Using the Server Access Assistant (DNAT)
Go to Protect | Rules and Policies | NAT rules
Click Add NAT rule
Click Server access assistant (DNAT)
Fill in the fields as you are prompted, then review the summary before clicking Save and Finish.
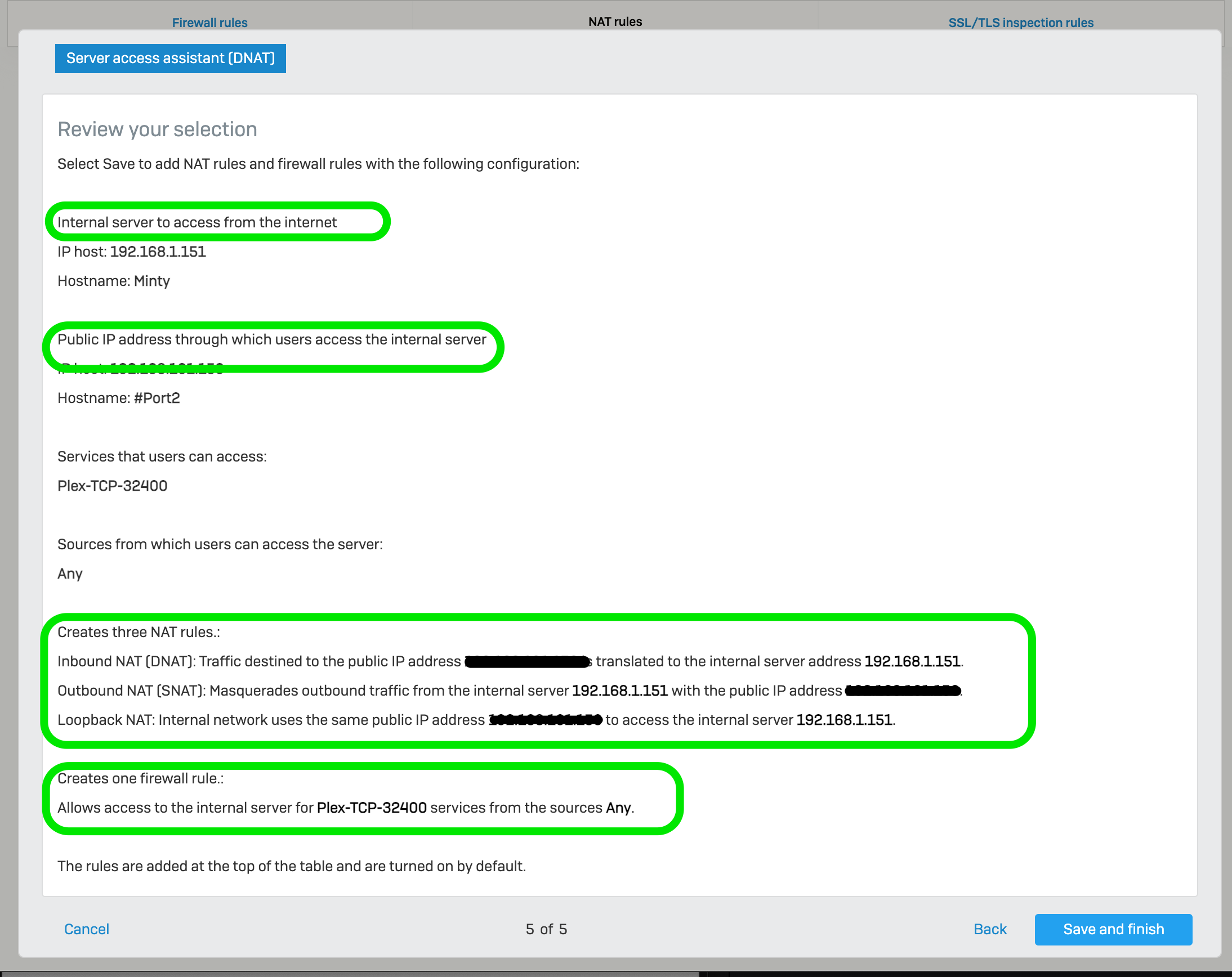
As the summary page shows, three NAT rules and one firewall rule will be created. While there is nothing wrong with using the Server Access Assistant (DNAT), the resulting NAT and firewall rules it creates can become a bit verbose, especially if you have multiple internal services that you want to make available.
Optimizing the NAT Rules created by Sophos XG’s Server Access Assistant (DNAT)
After completing the assistant, you end up with three NAT rules similar to what you see below:Let’s look at each rule and what it does:
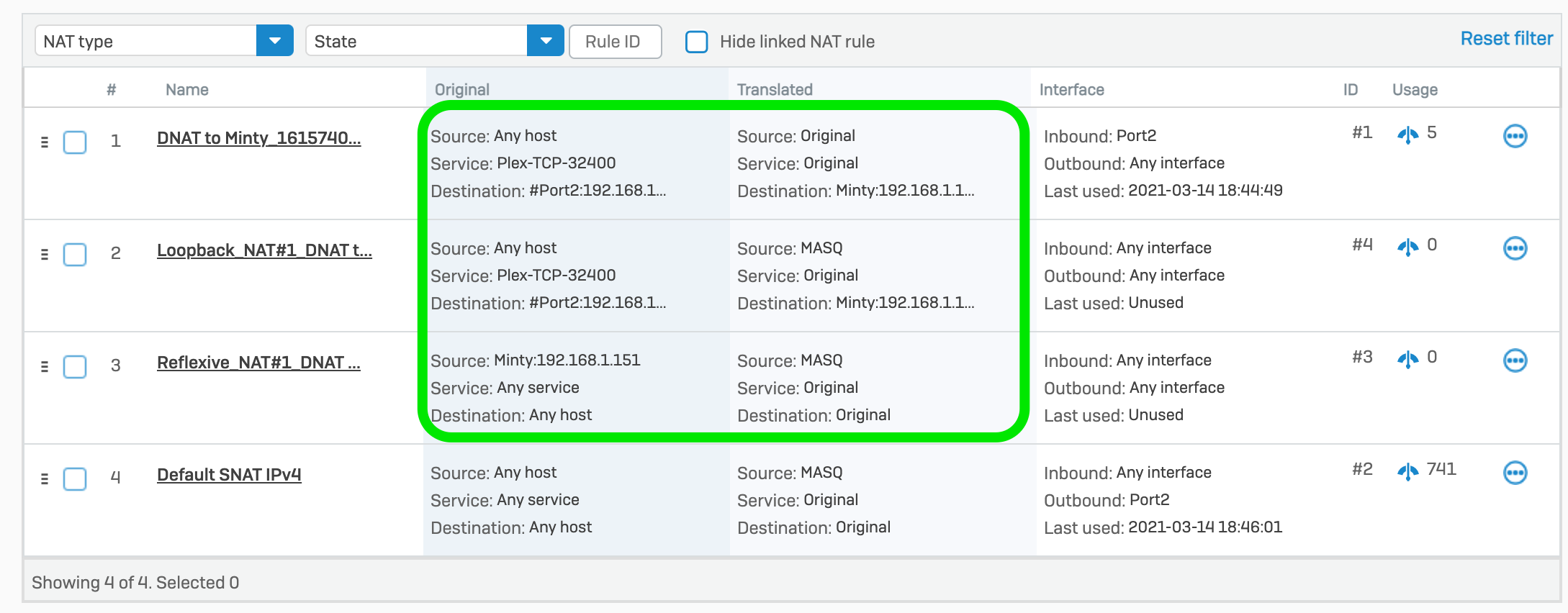
Rule 1 This will change the destination address from our public IP to the internal IP (DNAT).
Rule 2
This rule allows internal machines masquerading with the external IP due to SNAT through to the internal server. This is really only required if internal devices are attempting to use the public IP of the published service instead of the internal one. In practice, this would really only occur if you have a service configured with public DNS name resolution.
Rule 3
This rule allows traffic to flow from the internal server through to internal machines masquerading with the external IP due to SNAT. This would only be required if there was no default SNAT rule for outbound traffic, which you have probably already configured so that clients on the LAN can access the internet (see Rule 4 in the screenshot above)
By looking at the original and translated sections of the NAT rules we can see that the only rule we really require is Rule 1.
At this point, we can ironically see that by using the Server Access Assistant (DNAT), you end up getting two bonus SNAT rules that you don’t really need.
Once you understand what these auto-created rules are doing in relation to the rest of your rules and requirements, you may like to delete or disable Rule 2 and 3.
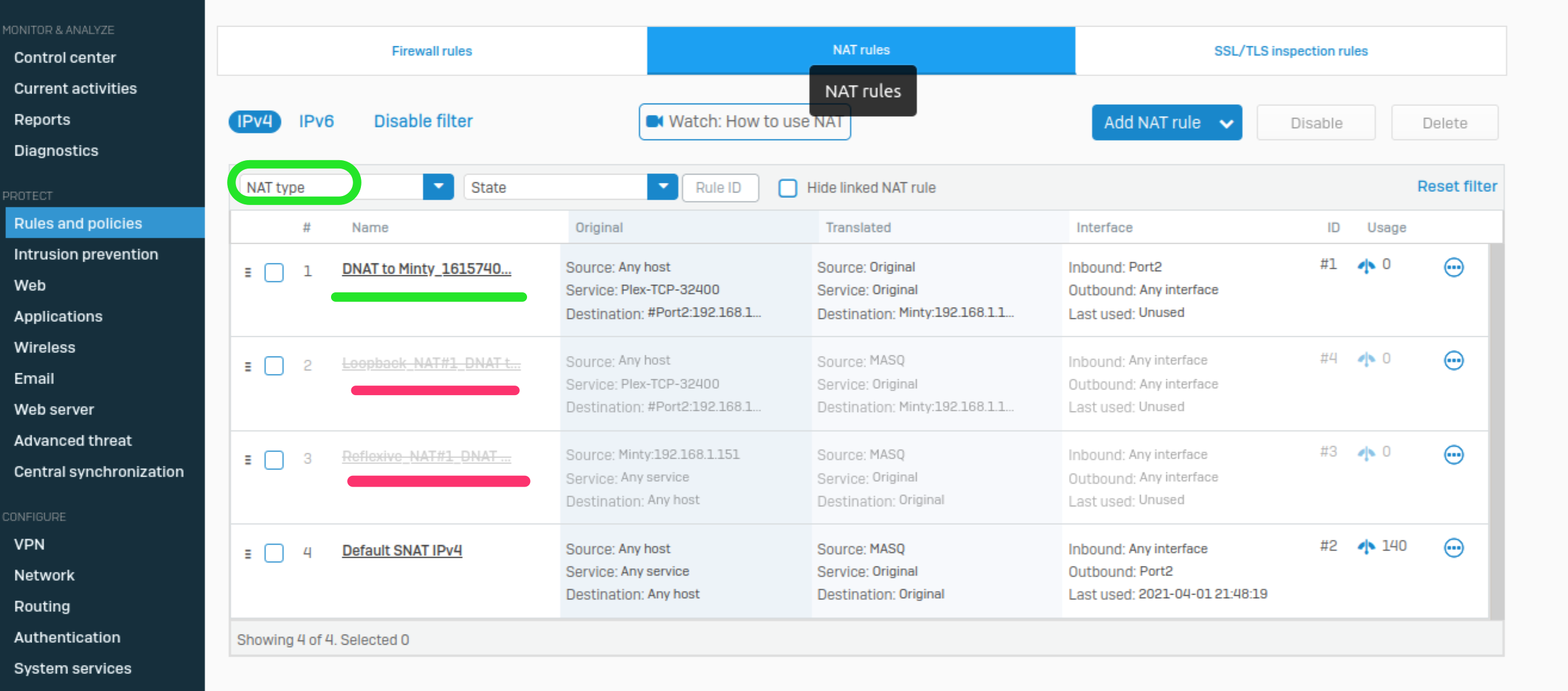
The Firewall Rule created by Sophos XG’s Server Access Assistant
To view the firewall rule created by the Server Access Assistant, go to Rules and Policies | Firewall Rules.
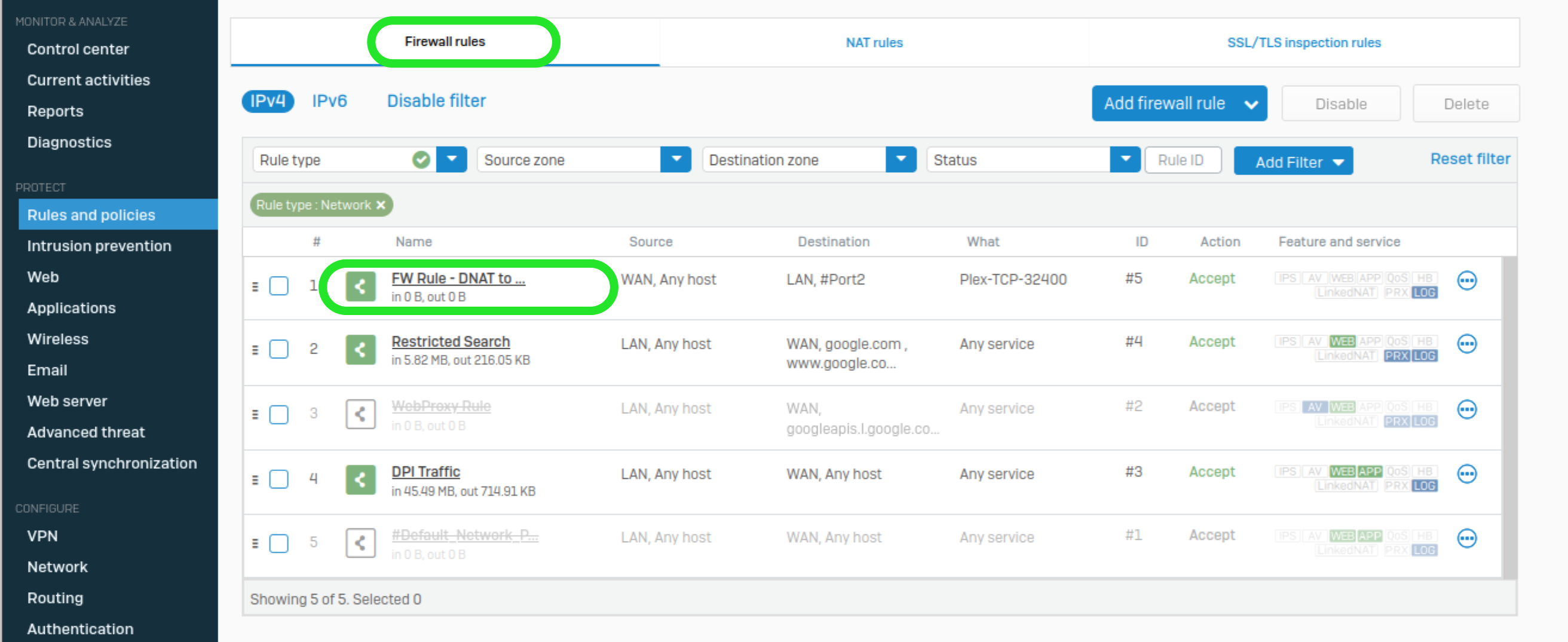
Let’s look at the Firewall rule’s settings:
Source
Zone: WAN
Source and Network and Devices: ANY
Destination and Services
Destination Zones: LAN
Destination Networks: #Port2 (the external interface / IP Address)
Services: Plex-TCP-32400
From this, we can tell that the rule does not allow traffic through to the internal IP address directly. Instead, it allows traffic that will be handled by the remaining DNAT rule. So, in fact you are allowing the DNAT traffic to flow.
Unlike the NAT rules, we do not need another explicit or implicit rule to allow traffic outbound from our internal address to be able to reply to the public address. This is because our firewall rules are stateful, meaning they track inbound and outbound conversations, and as such we don ’t need a rule for the ‘reply traffic’.
The NAT rules, on the other hand, are stateless. Unless there is a way to translate the source or destination address the traffic will simply not be sent to the correct location.
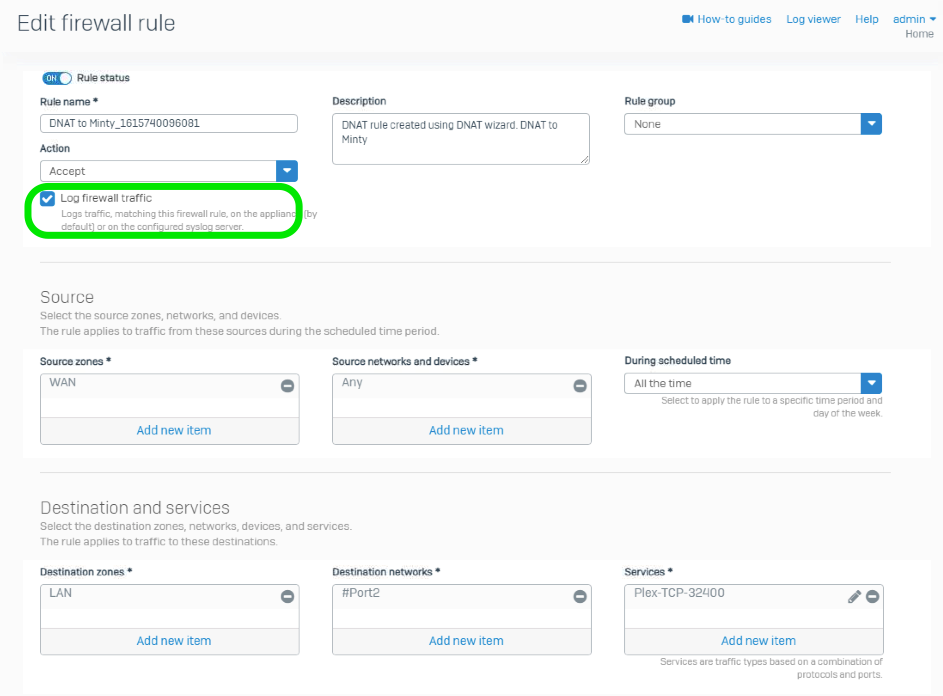
Something you should definitely do with the auto-created firewall rule, is enable the Log Firewall Traffic option.
You can then monitor its traffic using the live log viewer, and/or with Fastvue Sophos Reporter.
Go to Protect | Rules and Policies | Firewall Rules and edit the new rule that was created.
Check the box for “Log firewall traffic”
Save
Monitoring Firewall Rule Activity
Using Fastvue Reporter you can easily see what firewall rules are being used the most, and drill down into each one.
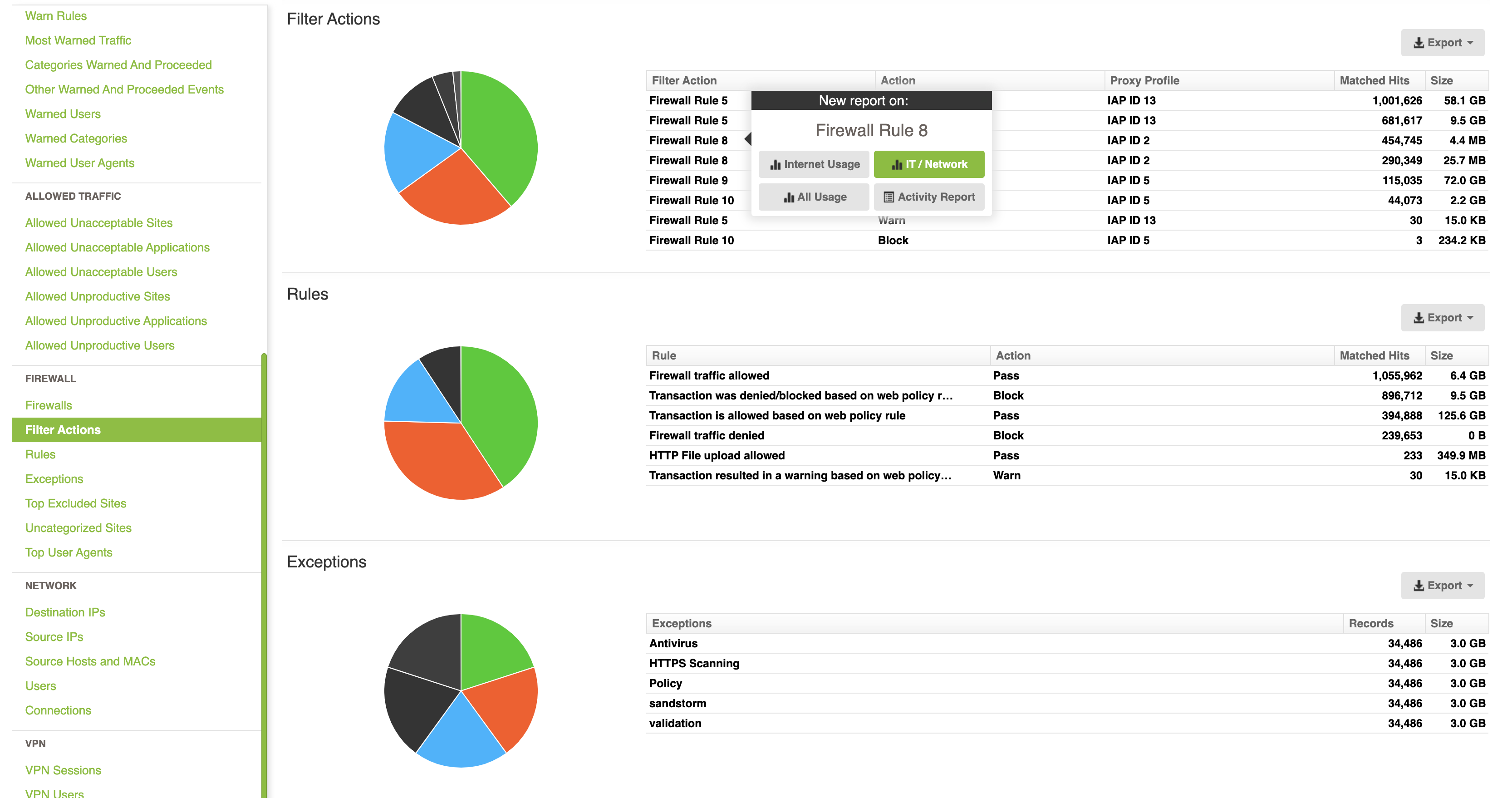
This provides a full report on all the traffic flowing through the rule, including what external IPs have been accessing the internal server the most.
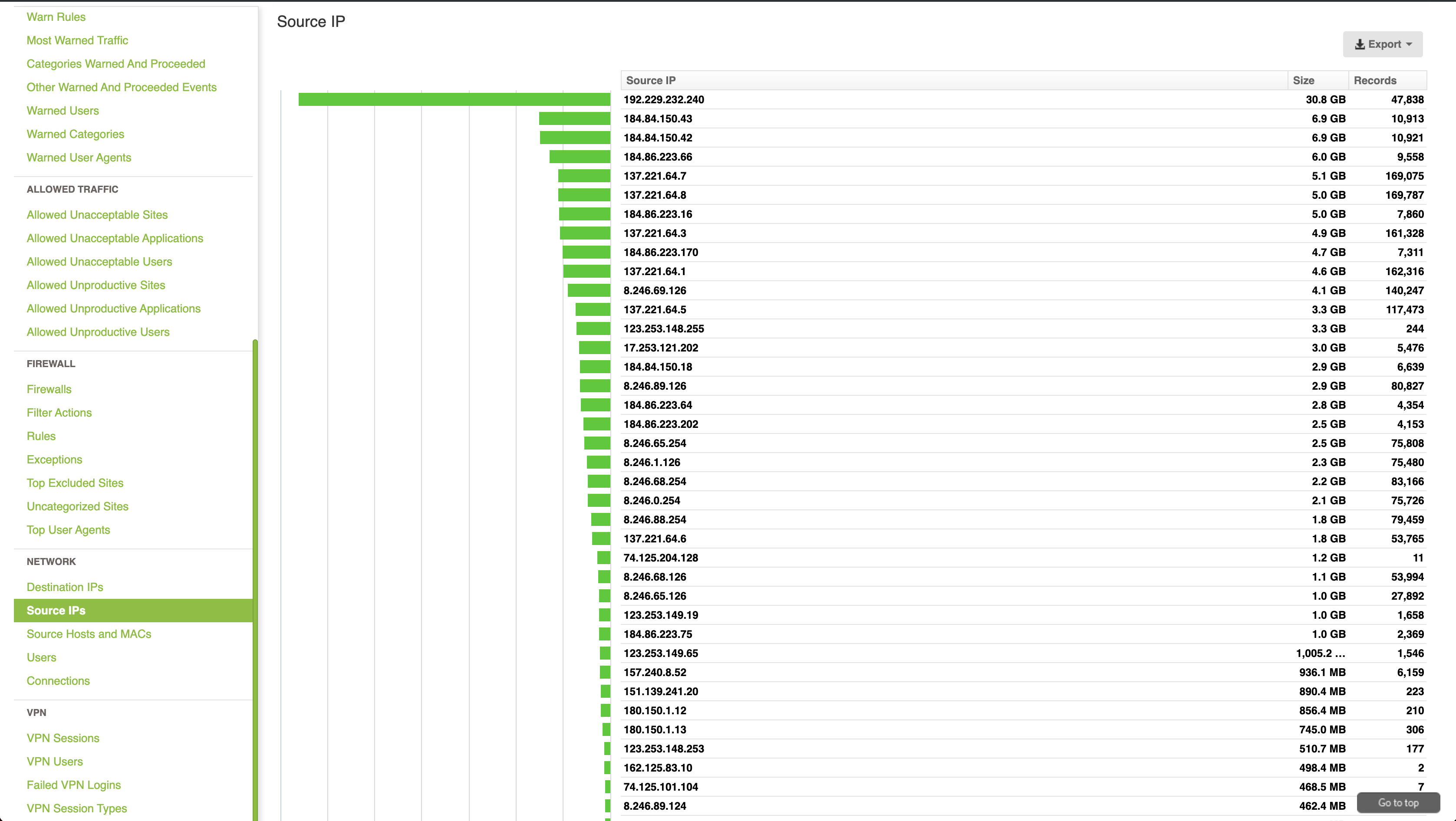
Regularly reporting on your firewall rules is important to keep your firewall ruleset clean and knowing what each rule is required for. If you do not maintain this over time you can end with rule sprawl which makes it harder to troubleshoot issues and can leave you with a firewall configuration that is open to traffic that is no longer required.
Conclusion
While it is convenient to use Sophos XG’s Server Access Assistant (DNAT) wizard, it does generate a lot of configuration that is not strictly required. By knowing your environment, some basic theory, and what is and is not required, you can manually configure clean concise DNAT rules.
When you encounter a more complex segmented network, you will have a better understanding of the different types of translations that are required and possible.
Try Sophos Reporter free, or learn more
- Share this storyfacebooktwitterlinkedIn